I rarely have a problem with a company to such an extent that I write off them off entirely. I have problems with Google and Facebook’s attitudes towards user privacy, but I still use Google Maps to navigate, and I still use Facebook Messenger to call my gran.
Twilio Inc., the developer of the Authy Two-factor authentication (2FA) app, is an exception.
As long as Twilio continues down its path of malicious design, I will never use Authy or any other app Twilio develops again. Yes, Authy is that bad.
Why?
1. Authy Locks Its Users In
Unlike most 2FA apps, Authy takes hostile steps to prevent you from leaving.
Take Google Authenticator for example. Google allows you to export your TOTP secret keys (I’m going to refer to these as “accounts” moving forward) as QR codes, which you can then scan and export into the app of your choice, such as Aegis.
Google Authenticator is far from the only 2FA app that allows for easy and efficient account transfers.
On its website, Ente Auth provides a non-exhaustive list of 2FA apps that can be exported from in a straightforward way. It includes most of the major ones:
2FAS Authenticator
Aegis Authenticator
Bitwarden
Google Authenticator
Raivo OTP
LastPass
Authy is notably missing from this list.
According to Authy’s website, in the interests of “security” (no elaboration provided), to export accounts you must follow this arduous process:
Login to the desired online account with your existing 2FA token.
Disable 2FA in the app's site.
Re-enable 2FA again in the app's site.
Scan the QR code, optionally write the Authentication Key, this time on the desired 2FA App.
If you are using 2FA on many of your accounts, this process will be long and painful.
Previously, there were workarounds.
For example, it was possible to use the Authy desktop app to efficiently export accounts.
This stopped working earlier this year, when Authy discontinued the desktop app.
It was also possible to transfer directly to Aegis if your Android phone was rooted. This has since been patched for most devices.
I personally had to go through the manual transfer process for many accounts, and it’s an experience I wouldn't wish on anyone.
The lack of transferability also means that there is no easy way to back up your accounts when using Authy. If Twilio disappears or Authy goes offline tomorrow and all your accounts are in Authy - you will be locked out of everything, potentially forever.
It Gets Worse
In painstakingly exporting my accounts from Authy, I discovered that some platforms won't allow you to disable TOTP 2FA without enabling another form of 2FA, such as SMS verification or installing push-notification apps.
So I had to hand over my phone number to companies I didn't want to give my phone number to, and install apps from companies I didn't want to install apps from, only to subsequently delete them, just to escape the Authy prison.
On some platforms, there appeared to be no option at all for disabling 2FA (for the purpose of transferring accounts) without emailing the platform's support.
I suppose this isn't entirely Authy's fault, but I still consider them somewhat complicit; it would have been easy for me to avoid if Authy wasn't so insistent on keeping my data hostage.
It Gets Worse Again
On one of the platforms I use relating to my work, it appears that Authy is the only option for 2FA. Authy or nothing, seriously.
Presumably, somehow Authy has convinced certain companies (Gemini is one major example, it also used to be the case with Twitch) to implement a 2FA option that is entirely based around Authy’s non-standard solution using 7 digit 2FA codes that seem to only work with Authy. Madness.
2. Authy Locks Its Users Out
Ironically, just as it locks its users in, Authy also has a tendency to lock its users out.
People who used Authy’s desktop app for many years were locked out of using the app when it was discontinued. The same goes for its Chrome app and extension.
These users were forced to move over to using Authy’s mobile apps.
But many users were locked out of using the mobile apps as well - with no way of accessing their Authy accounts at all! I was one of them.
In the interests of “security”, again, Authy has recently decided to entirely lock out users of the specifically designed-for-security Android-based GrapheneOS. Authy has chosen to use Google’s Play Integrity API in a way that achieves this outcome. According the GrapheneOS developers over on Mastodon:
Authy's response about their usage of the Play Integrity API shows their service is highly insecure and depends on having client side validation. Play Integrity is thoroughly insecure and easily bypassed, so it's unfortunate that according to Authy their security depends on it.
If Authy insists on using it, they should use the standard Android hardware attestation API to permit using GrapheneOS too. It's easy to do.
[…]
Banning 250k+ people with the most secure smartphones from using your app is anti-security, not pro-security.
I use GrapheneOS personally. I have had no functionality issues with any app other than Authy. With sandboxed Google Play, all my apps for work function perfectly, my banking apps work perfectly, but Authy?
Authy wouldn’t let me log in. They locked me in to their ecosystem, then they locked me out.
The only way I was able to eventually access my Authy account to work around this insanity was by installing the app on an old Nokia 2.3 I had lying around that runs Android 11 and received its final security patch in February 2022. Make it make sense.
3. Assorted Grievances
Authy’s Habit of Getting Hacked
4 July 2024, Twilio Confirms Data Breach After Hackers Leak 33 Million Authy User Phone Numbers 🙄
“The threat actor seems to have obtained the information by inputting a massive list of phone numbers into Authy’s unsecured API endpoint, which would then verify whether they’re associated with the app.”
I get it, hacks happen. Leaks happen. But 33 million phone numbers because you have an unsecured API endpoint, when you’re supposed to be in the security business? It’s iffy - and it’s not their first breach either:
9 August 2022, Twilio suffers data breach after its employees were targeted by a phishing campaign
Digital communication platform Twilio was hacked after a phishing campaign tricked its employees into revealing their login credentials. The company disclosed the data breach in a post on its blog, noting that only “a limited number” of customer accounts were affected by the attack.
10 May 2021, Twilio, HashiCorp Among Codecov Supply Chain Hack Victims
Our subsequent investigation into the impact of this event found that a small number of email addresses had likely been exfiltrated by an unknown attacker as a result of this exposure.
Authy is Closed-Source -
- if you care about that.
I do, especially when there are open-source apps that are just as user-friendly and functional. I generally like being able to verify exactly what data of mine is being gobbled up. I haven’t analysed it in depth, but it doesn’t help that Authy’s privacy policy appears to be quite wide-ranging.
Options like Aegis, Bitwarden, and Ente Auth are all open-source.
Authy is Susceptible to Sim-Swapping Attacks
Because Authy uses your phone number as the basis of its account recovery mechanisms, it is more susceptible to sim-swapping attacks. The risk is probably heightened now that the phone numbers of 33 million Authy users were leaked online earlier this year, as referenced above.
Authy is Less Functional than the Alternatives
I’m going to get a little petty, just to cap things off.
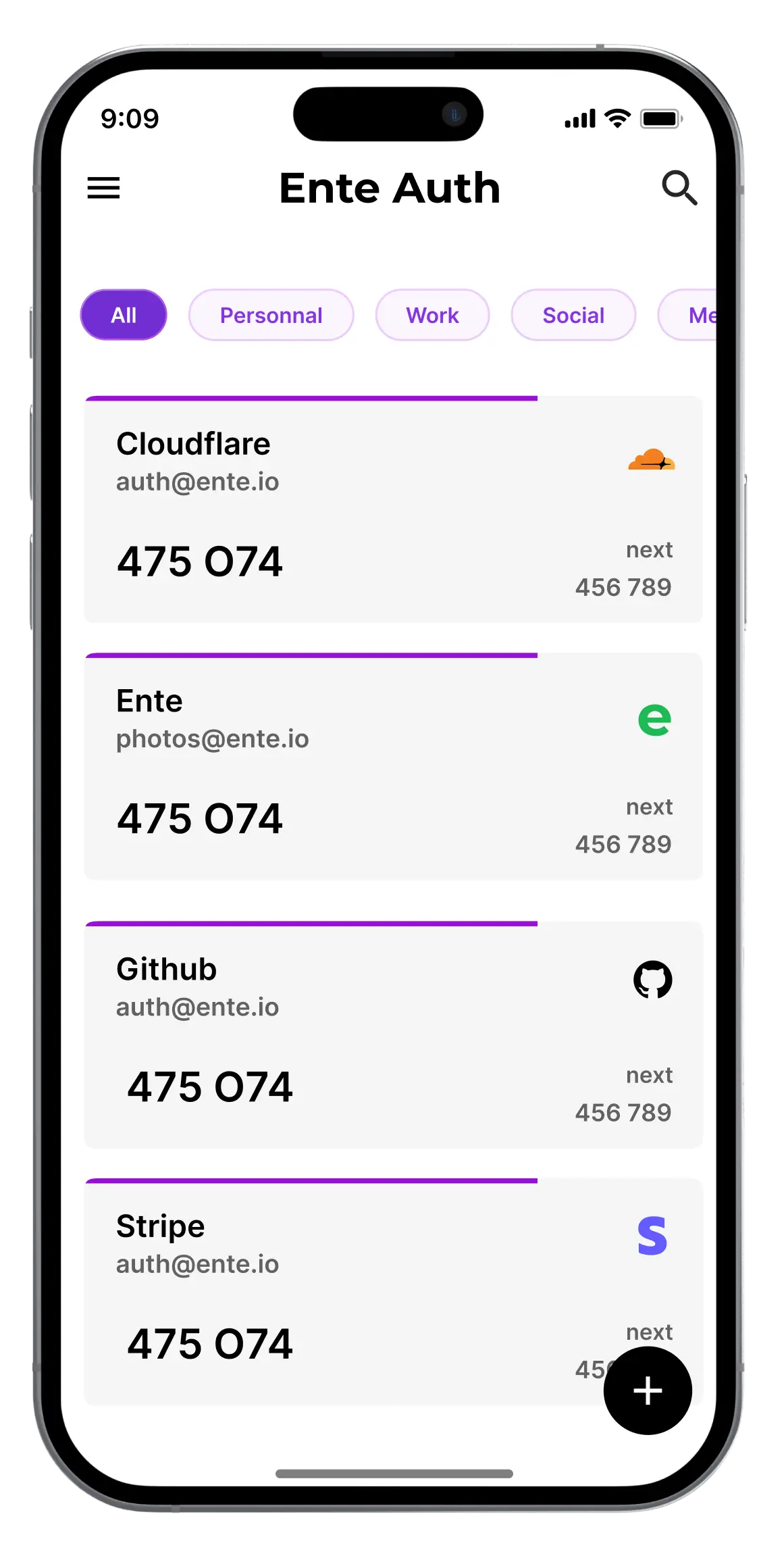
I use Ente Auth. Ente Auth has features some people will have issues with (the fact I can log in and access my TOTP codes through a web app will be disconcerting to some, notwithstanding that it is fully end-to-end encrypted). TOTP has issues in and of itself.
Setting that aside, as far as user experience goes, and I know this is subjective, Ente Auth is better than Authy. It shows me what the next code will be (and allows me to copy that code with one tap). It allows for easy tagging:
Authy doesn’t:
Authy is also ugly. Ente Auth is sexy.
Damn I hate Authy.